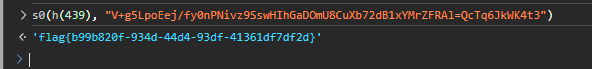WEB
2048*16
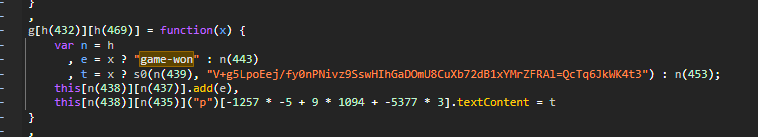
审计源码可以看到可疑点
进行单步调试,跳到 js 界面
此时就可以进入控制台查看可疑代码
n=h 所以我们看看 h 是什么
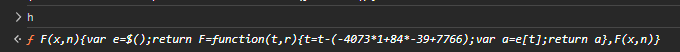
发现指向 F ,直接传参试试
得到
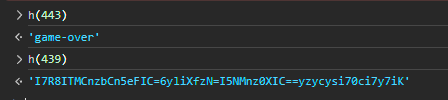
直接调用 s0 看看
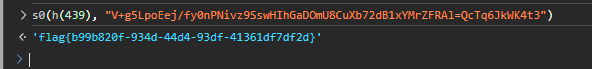
结束
flag{b99b820f-934d-44d4-93df-41361df7df2d}
Bypass it
提示需要登录,没有账户所以需要注册
点击弹 alert 根据提示 This page requires javascript to be enabled :)
把浏览器 禁用Javascript 开了就行
进注册界面注册个号再登录就行,登录记得把 禁用Javascript 关了
hgame{2d2f501efc15bd17039eb7e73f3206dd3d62b19c}
Select Courses
玄学题,等官方WP…
ezHTTP
经典题
1
| curl -i http://47.102.130.35:31673 --header "Referer: vidar.club" --header "User-Agent: Mozilla/5.0 (Vidar; VidarOS x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36 Edg/121.0.0.0" --header "X-Real-IP: 127.0.0.1"
|
得到一串 jwt
1
| eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJGMTRnIjoiaGdhbWV7SFRUUF8hc18xbVAwclQ0bnR9In0.VKMdRQllG61JTReFhmbcfIdq7MvJDncYpjaT7zttEDc
|
JSON Web Tokens - jwt.io解得
hgame{HTTP_!s_1mP0rT4nt}
RE
ezASM
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
| section .data
c db 74, 69, 67, 79, 71, 89, 99, 113, 111, 125, 107, 81, 125, 107, 79, 82, 18, 80, 86, 22, 76, 86, 125, 22, 125, 112, 71, 84, 17, 80, 81, 17, 95, 34
flag db 33 dup(0)
format db "plz input your flag: ", 0
success db "Congratulations!", 0
failure db "Sry, plz try again", 0
section .text
global _start
_start:
; Print prompt
mov eax, 4
mov ebx, 1
mov ecx, format
mov edx, 20
int 0x80
; Read user input
mov eax, 3
mov ebx, 0
mov ecx, flag
mov edx, 33
int 0x80
; Check flag
xor esi, esi
check_flag:
mov al, byte [flag + esi]
xor al, 0x22
cmp al, byte [c + esi]
jne failure_check
inc esi
cmp esi, 33
jne check_flag
; Print success message
mov eax, 4
mov ebx, 1
mov ecx, success
mov edx, 14
int 0x80
; Exit
mov eax, 1
xor ebx, ebx
int 0x80
failure_check:
; Print failure message
mov eax, 4
mov ebx, 1
mov ecx, failure
mov edx, 18
int 0x80
; Exit
mov eax, 1
xor ebx, ebx
int 0x80
|
审计(GPT)得 check_flag 中进行了异或
也就是把 74, 69, 67, 79, 71, 89, 99, 113, 111, 125, 107, 81, 125, 107, 79, 82, 18, 80, 86, 22, 76, 86, 125, 22, 125, 112, 71, 84, 17, 80, 81, 17, 95, 34 跟 0x22 进行异或就可以得到flag
1
2
3
4
5
6
7
8
|
data = [74, 69, 67, 79, 71, 89, 99, 113, 111, 125, 107, 81, 125, 107, 79, 82, 18, 80, 86, 22, 76, 86, 125, 22, 125, 112, 71, 84, 17, 80, 81, 17, 95, 34]
result = ''.join(chr(i ^ 0x22) for i in data)
print(result)
|
hgame{ASM_Is_Imp0rt4nt_4_Rev3rs3}
ezPYC
用 pyinstxtractor 把 exe 解包成 pyc
然后用python反编译 - 在线工具 (tool.lu)或者 uncompyle6 反编译得
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
|
flag = [
87,
75,
71,
69,
83,
121,
83,
125,
117,
106,
108,
106,
94,
80,
48,
114,
100,
112,
112,
55,
94,
51,
112,
91,
48,
108,
119,
97,
115,
49,
112,
112,
48,
108,
100,
37,
124,
2]
c = [
1,
2,
3,
4]
input = input('plz input flag:')
for i in range(0, 36, 1):
if ord(input[i]) ^ c[i % 4] != flag[i]:
print('Sry, try again...')
exit()
continue
print('Wow!You know a little of python reverse')
return None
|
也是异或,稍微改一下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
|
flag = [
87,
75,
71,
69,
83,
121,
83,
125,
117,
106,
108,
106,
94,
80,
48,
114,
100,
112,
112,
55,
94,
51,
112,
91,
48,
108,
119,
97,
115,
49,
112,
112,
48,
108,
100,
37,
124,
2,
]
c = [1, 2, 3, 4]
flagG = ""
for i in range(0, 37, 1):
flagG += chr(flag[i] ^ c[i % 4])
print(flagG)
|
VIDAR{Python_R3vers3_1s_1nter3st1ng!}
ezUPX
把文件脱壳放入ida得
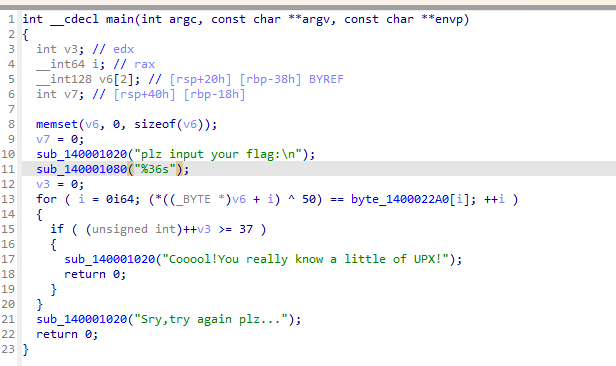
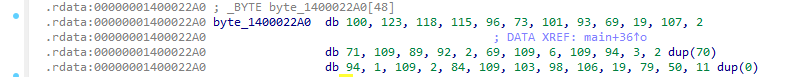
也是异或
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
| data = (
[
100,
123,
118,
115,
96,
73,
101,
93,
69,
19,
107,
2,
71,
109,
89,
92,
2,
69,
109,
6,
109,
94,
3,
]
+ [70, 70]
+ [94, 1, 109, 2, 84, 109, 103, 98, 106, 19, 79, 50]
+ [0] * 11
)
result = "".join(chr(i ^ 50) for i in data)
print(result)
|
VIDAR{Wow!Y0u_kn0w_4_l1ttl3_0f_UPX!}
ezIDA
ida打开就行
hgame{W3lc0me_T0_Th3_World_of_Rev3rse!}
CRYPTO
ezRSA
题目:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| from Crypto.Util.number import *
from secret import flag
m=bytes_to_long(flag)
p=getPrime(1024)
q=getPrime(1024)
n=p*q
phi=(p-1)*(q-1)
e=0x10001
c=pow(m,e,n)
leak1=pow(p,q,n)
leak2=pow(q,p,n)
print(f'leak1={leak1}')
print(f'leak2={leak2}')
print(f'c={c}')
"""
leak1=149127170073611271968182576751290331559018441805725310426095412837589227670757540743929865853650399839102838431507200744724939659463200158012469676979987696419050900842798225665861812331113632892438742724202916416060266581590169063867688299288985734104127632232175657352697898383441323477450658179727728908669
leak2=116122992714670915381309916967490436489020001172880644167179915467021794892927977272080596641785569119134259037522388335198043152206150259103485574558816424740204736215551933482583941959994625356581201054534529395781744338631021423703171146456663432955843598548122593308782245220792018716508538497402576709461
c=10529481867532520034258056773864074017027019578041866245400647840230251661652999709715919620810933437191661180003295923273655675729588558899592524235622728816065501918076120812236580344991140980991532347991252705288633014913479970610056845543523591324177567061948922552275235486615514913932125436543991642607028689762693617305246716492783116813070355512606971626645594961850567586340389705821314842096465631886812281289843132258131809773797777049358789182212570606252509790830994263132020094153646296793522975632191912463919898988349282284972919932761952603379733234575351624039162440021940592552768579639977713099971
"""
|
脚本:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| from Crypto.Util.number import *
e = 0x10001
leak1 = 149127170073611271968182576751290331559018441805725310426095412837589227670757540743929865853650399839102838431507200744724939659463200158012469676979987696419050900842798225665861812331113632892438742724202916416060266581590169063867688299288985734104127632232175657352697898383441323477450658179727728908669
leak2 = 116122992714670915381309916967490436489020001172880644167179915467021794892927977272080596641785569119134259037522388335198043152206150259103485574558816424740204736215551933482583941959994625356581201054534529395781744338631021423703171146456663432955843598548122593308782245220792018716508538497402576709461
c = 10529481867532520034258056773864074017027019578041866245400647840230251661652999709715919620810933437191661180003295923273655675729588558899592524235622728816065501918076120812236580344991140980991532347991252705288633014913479970610056845543523591324177567061948922552275235486615514913932125436543991642607028689762693617305246716492783116813070355512606971626645594961850567586340389705821314842096465631886812281289843132258131809773797777049358789182212570606252509790830994263132020094153646296793522975632191912463919898988349282284972919932761952603379733234575351624039162440021940592552768579639977713099971
phi = (leak1 - 1) * (leak2 - 1)
d = pow(e, -1, phi)
m = pow(c, d, leak1 * leak2)
print(long_to_bytes(m))
|
hgame{F3rmat_l1tt1e_the0rem_is_th3_bas1s}
MISC
Simple Attack
ZIP明文攻击,使用 ARCHPR
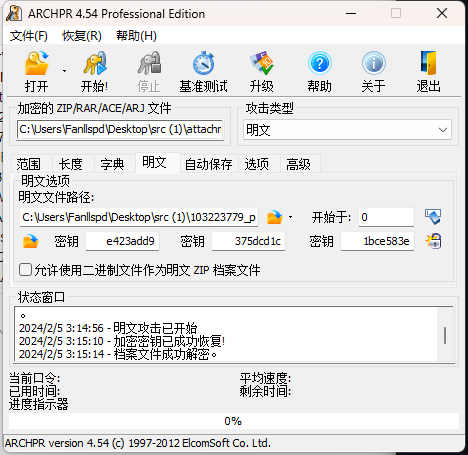
解密得到 base64 图片
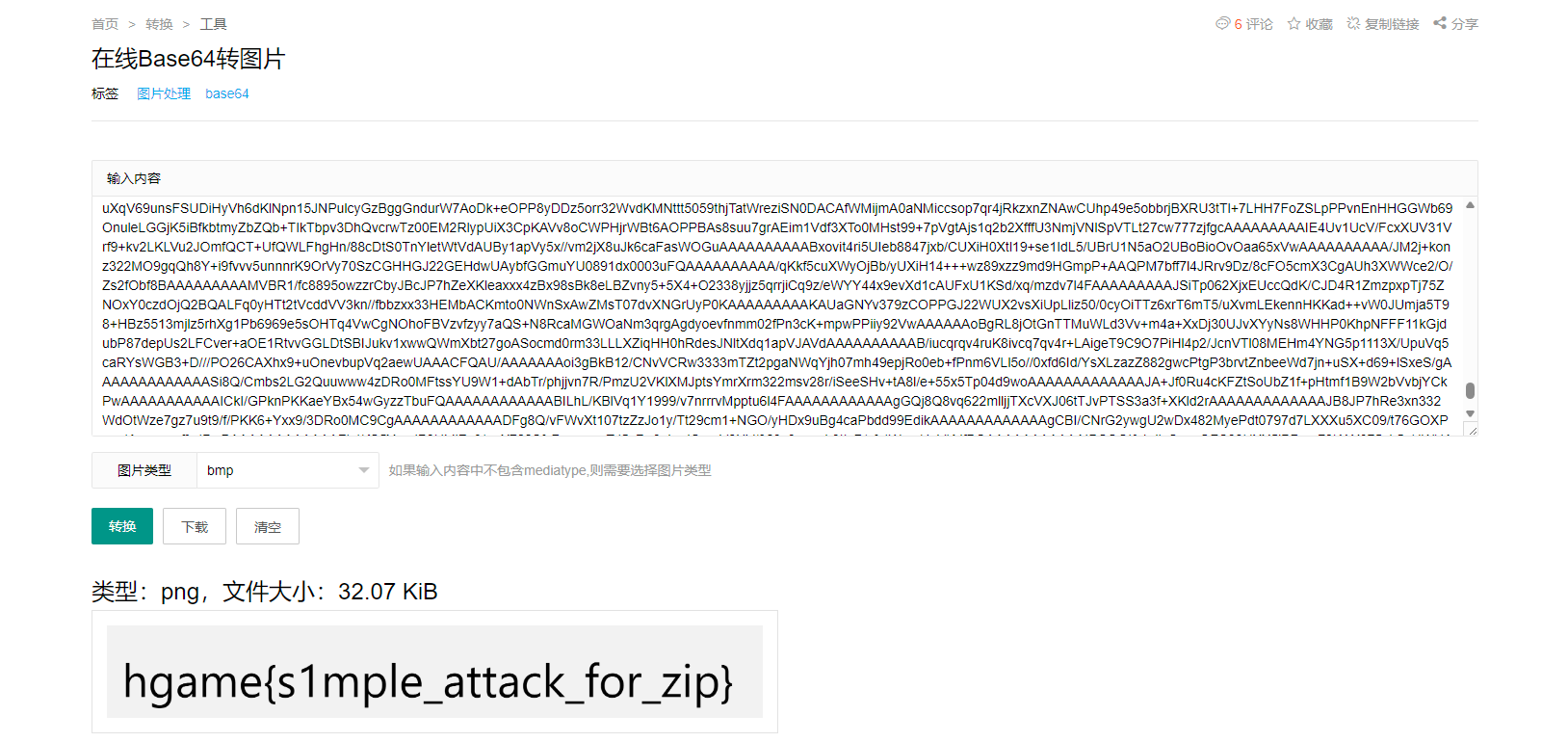
来自星尘的呼唤
一个即将发售的游戏的主角薇^3带来了一条消息。这段消息隐藏在加密的图片里 但即使解开了图片的六位弱加密,看到的也是一张迷惑的图片。 也许游戏的官网上有这种文字的记录? 补充:flag格式为hgame\{[a-z0-9_]+\}
弱密码猜测123456
1
| steghide extract -sf xxx.jpg -p 123456
|
得到图片和前端网页,看了 js ,猜测要去游戏官网下载字体,得到
希儿希儿希儿
Ch405是一名忠实的希儿厨,于是他出了一道这样的题,不过他似乎忘了这个加密的名字不是希儿了(x虽然经常有人叫错 补充: 图片打不开是正常现象,需要修复 最终得到的大写字母请用hgame{}包裹
根据提示猜测是希尔加密,图片需要根据 crc 还原宽高
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| import binascii
import struct
crcbp = open("secret.png", "rb").read()
crc32frombp = int(crcbp[29:33].hex(), 16)
print(crc32frombp)
for i in range(4000):
for j in range(4000):
data = crcbp[12:16] + struct.pack(">i", i) + struct.pack(">i", j) + crcbp[24:29]
crc32 = binascii.crc32(data) & 0xFFFFFFFF
if (
crc32 == crc32frombp
):
print(i, j)
print("hex:", hex(i), hex(j))
|
得到
1
2
3
| 303792205
1394 1999
hex: 0x572 0x7cf
|
通过 stegsolver 打开,得到
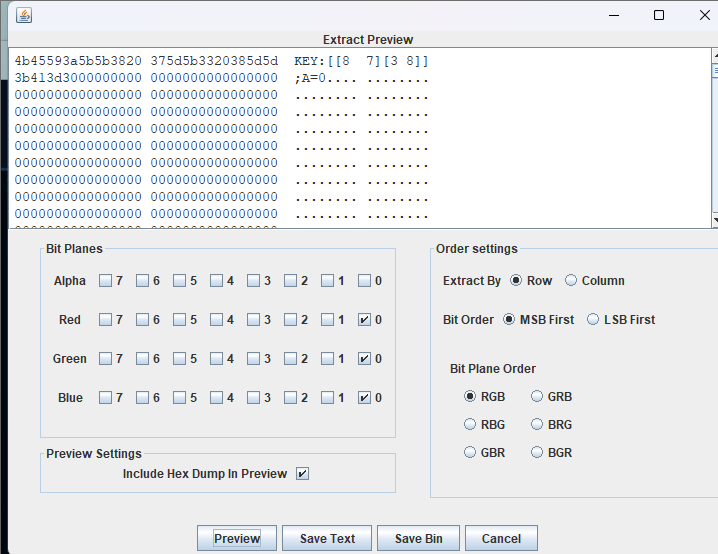
用 foremost
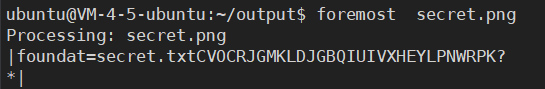
得到 CVOCRJGMKLDJGBQIUIVXHEYLPNWR
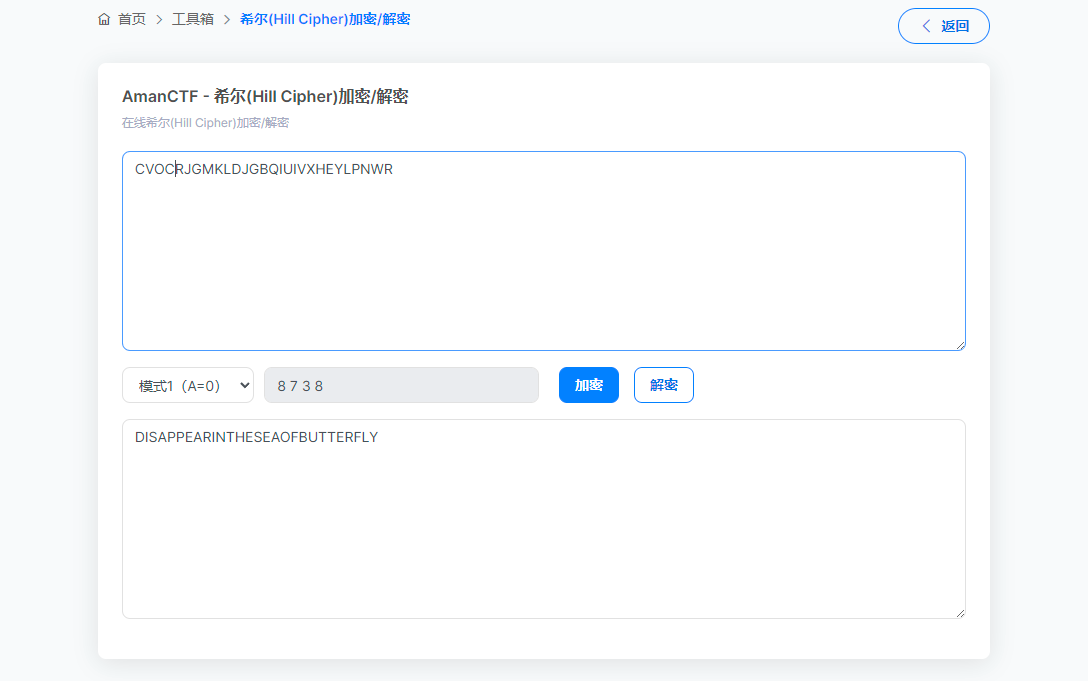
hgame{DISAPPEARINTHESEAOFBUTTERFLY}